To perform a complex multi-step cybersecurity function, would you rather run a suite of tools (each limited to certain steps) or use a single automated platform?
A CTEM platform is a cybersecurity solution for automating and managing continuous threat exposure management (CTEM) processes (including asset scoping, prioritization, and validation) in one place, i.e., “a single pane of glass.”
At Element Security, we offer a powerful, externally focused CTEM platform. Learn more here.
Using a CTEM platform, an organization can centralize and automate CTEM workflows. Without a CTEM platform, a security team would require an extensive suite of tools, complex project management, and manual work to perform CTEM.
The benefit of taking a platform approach to CTEM cannot be underestimated. 42% of organizations say that their number one challenge in threat detection and remediation is an overabundance of tools.
The rest of this article is based on our experience building a leading CTEM platform.
What is Continuous Threat Exposure Management?
Continuous threat exposure management (CTEM) is a pragmatic and systemic approach organizations can use to continually evaluate the accessibility, exposure and exploitability of digital and physical assets.
Put more simply, CTEM is a series of processes that help you find and filter out the number of potential paths someone might take to hack you and prioritize your efforts to stop them.
The goal of CTEM is to find the potential exposures that could cause real business risk and need rapid mitigation or remediation, pinpoint the exact fixes to reduce the threat exposure they create, and manage your response efforts. All in a consolidated way.
Instead of doing pen testing, threat monitoring, vulnerability scanning, and other offensive security practices as separate actions and prioritizing fixes based on CVEs and infrastructure-led thinking, CTEM forces an organization to approach security based on threat intelligence and business-specific risks.
CTEM also moves offensive security and remediation processes from actions that happen “sometime” to a system that happens “all the time” and brings different stakeholders like IT teams into the entire process.
Gartner predicts that organizations that do CTEM will suffer 60% fewer breaches than companies that do not – all other things being equal.
To make this kind of continuous security optimization possible, CTEM breaks down proactive security into five continuous processes called stages.
The 5 stages of continuous threat exposure management
While the practical technical solutions used in each CTEM stage can vary, we think it helps to consider the entire CTEM process as a series of questions.
Each stage of CTEM asks and answers new questions about IT environments to find out exactly where risks are and plan the most efficient and impactful fixes.
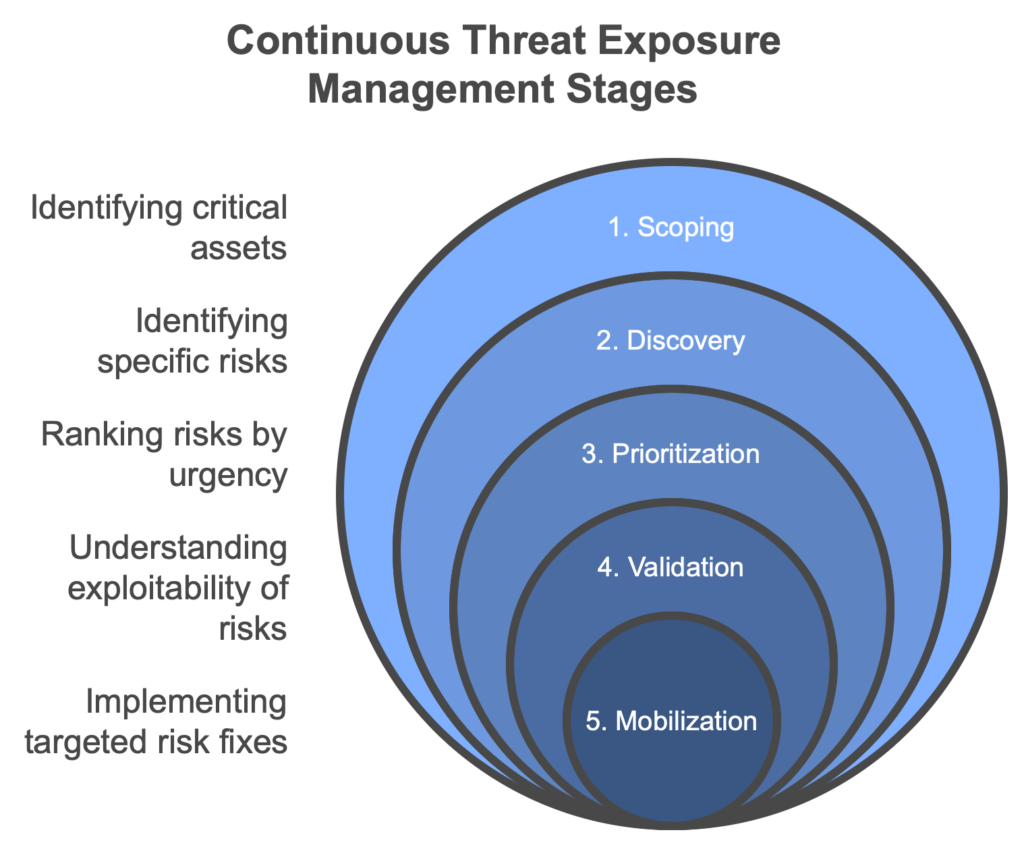
The five CTEM stages are:
1. Scoping
The first stage of CTEM asks, “What are the processes that are important to me from a threat exposure standpoint?”
Scoping tells you “what” resources put your business at risk.
Scoping is the process of discovering your IT environment (and everything connected to it), e.g., apps, servers, websites, etc., and narrowing that down to a list of assets that, if compromised, would damage your organization in some way.
Scoping is where you find out:
- Potential sources of data exposure.
- Systems that, if compromised, would cause damage.
- Potential lateral movement paths into critical environments.
- What systems are not actually dangerous to the organization.
- Other business risks that your IT assets create.
2. Discovery
Discovery builds on the initial list of assets created during scoping and asks, “How do we discover risks within this scope?”
Discovery tells you “where” risks might occur.
This stage discovers the specific risks to the resources found during the scoping stage. It tells you how your IT resources could be attacked.
For example, if scoping told you that your business has regulated personally identifiable information (PII) stored in cloud environments, discovery is where you’d map out a list of cloud management consoles that would allow exposure if compromised.
3. Prioritization
The first two CTEM stages (scoping and discovery) aim to discover the unique list of risks in your environment. However, especially in cloud or hybrid cloud environments, this will be a very big list.
The next stage is to narrow this list further to prioritize which potential risks to investigate right now and which ones can wait.
Prioritization is finding out “when” to tackle certain risks.
Prioritization is matching your business’s resources to threat intelligence. It’s understanding what resources face the most risk right now. For example, this is the stage where an organization might find out that their cloud buckets are vulnerable to the current wave of brute force credential compromise attempts.
4. Validation
From the prioritization stage, you know what your business-critical risks are and how they relate to current threat intelligence. Now, you need to learn how exactly those theoretical risks are exploitable.
Validation tells us “how” risks could be exploited.
This stage starts with theoretical approximations of risk and then finds out your real-world risk.
You need to approach your environment like a hacker would to see what exploitation paths are really present.
This stage is critical to the CTEM process as it will directly inform how you reduce risks in the next phase.
5. Mobilization
The final stage is getting all the relevant stakeholders involved (or “mobilized”) to fix the risks identified during the previous CTEM stages.
Mobilization is determining “which” risks to fix and which fixes to use.
While some risks might be mitigated (for example, through new firewall rules or enforcing 2FA), others might need immediate remediation to totally eliminate them.
The core benefit of CTEM is that when you get to this stage, you know exactly where to focus your efforts alongside other stakeholders in IT and DevOps to make your organization fundamentally more secure.
What Is a CTEM Platform?
A CTEM platform is the most efficient way to get CTEM benefits.
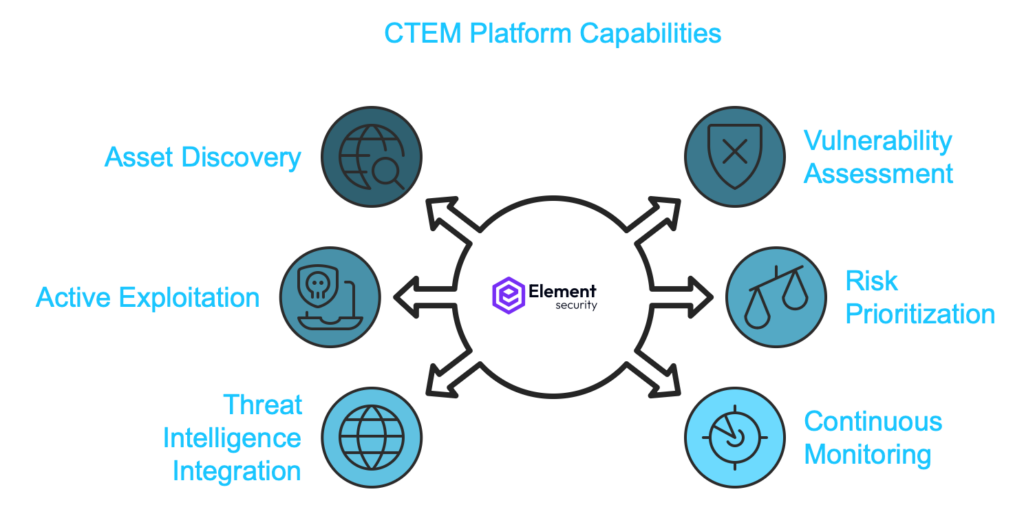
This is because the CTEM stages outlined above are interlinked processes that work best when done through a single platform.
A CTEM platform’s capabilities should include:
Asset Discovery
- Continuous scanning and identification of all internet-facing assets.
- Centralized inventory with real-time visibility of the attack surface.
Vulnerability Assessment
- Automated detection of vulnerabilities, misconfigurations, and weak points.
Exploitation:
- Active exploitation of vulnerabilities to generate Proof of Concept (PoC).
- Full attack chain simulations to understand the actual risk and impact.
Risk Prioritization
- Prioritization of vulnerabilities based on exploitability and business impact.
- Clear guidance for remediation efforts, focusing on high-risk issues.
Threat Intelligence Integration
- Real-time updates of threat landscapes and newly discovered vulnerabilities.
- Integration with external threat intelligence feeds.
Continuous Monitoring and Validation
- Ongoing attack surface monitoring and validation of security controls.
- Simulation of new attack methods to test resilience over time.
Remediation Guidance
- Actionable remediation steps for each vulnerability.
- Integration with ticketing systems to streamline remediation processes.
Reporting and Analytics
- Detailed reports with insights on vulnerabilities, attack paths, and fixes.
- Real-time dashboards for tracking security posture improvements.
Automation and Scalability
- Ability to automate scanning, validation, and remediation workflows.
- Scalable across large environments with multiple assets and attack vectors.
Compliance and Regulatory Support
- Compliance monitoring for frameworks like PCI-DSS, GDPR, etc.
- Audit-ready reports for security and compliance assessments.
All of these are essential parts of the CTEM process.
An organization could perform each of these tasks with different tools. For example, network scanners to help with scoping, threat intelligence feeds and vulnerability scanners for discovery, and Attack Surface Management (ASM) or Breach Attack Simulation (BAS) tools to partially cover some CTEM stages.
However, taking a point solution approach to CTEM would be time-consuming, technically complex, and potentially risky due to the likelihood of gaps in risk understanding.
A fit-for-purpose CTEM platform like Element Security consolidates CTEM into a single tool type.
What to Look for In a CTEM Platform
A CTEM platform like Element Security can consolidate the entire CTEM process.
But that’s not the case for all platforms that call themselves “CTEM.” Most so-called CTEM platforms only cover some CTEM stages. Many focus on asset discovery or mapping but fail to perform vital CTEM validation tasks such as active exploitation.
This difference matters because, without a complete chain of CTEM capabilities, including validation, organizations will not get an accurate picture of their threat exposure. They also risk excessive false positives.
For example, consider a situation where a CTEM platform discovers a CVE in an in-scope asset.
- Platform A is capable of active exploitation. It can test the asset, determine that it is not exploitable in its current state, and move on to another target. No false positives.
- Platform B does not do active exploitation. It will trigger an alert based on the CVE version with no context as to whether it is actually dangerous. A security team will investigate and discover that the CVE is not exploitable. False positive.
Without active exploitation, there is no validation.
Active exploitation shows you exposures in real time, cuts out the vast majority of false alerts, reduces noise, and protects your team from alert fatigue.
As a rule, a CTEM platform cannot do validation without active exploitation. This means that most solutions that call themselves “CTEM” cannot actually complete the entire CTEM process by themselves.

Element Security CTEM Platform
Element Security doesn’t do simulations of attacks; we do actual attacks.
Element Security’s CTEM platform works externally from a black box perspective, bringing you the actual point of view of a hacker and their capabilities.
No other CTEM platform completes the full CTEM cycle.
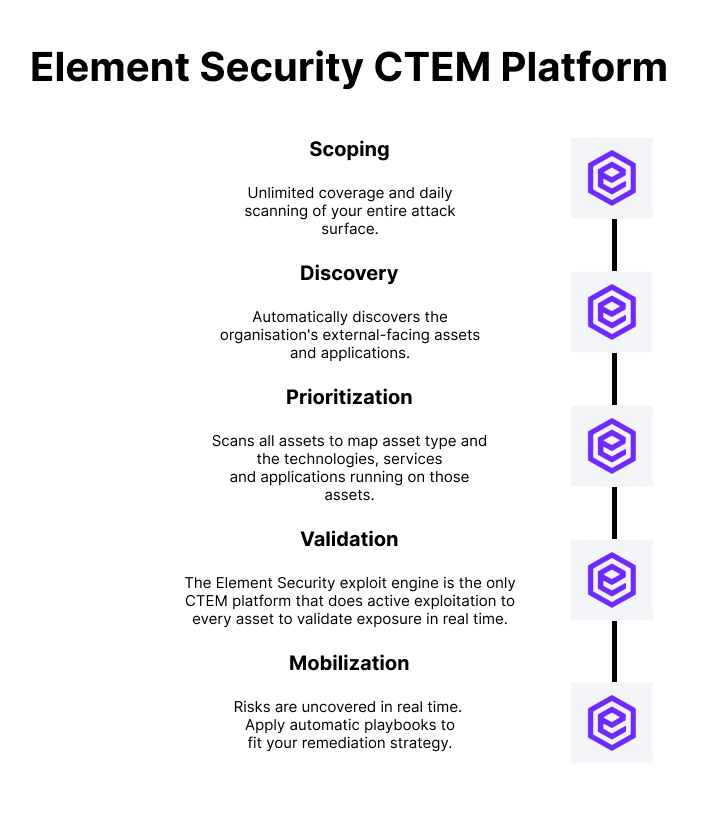
With Element Security, deployment takes less than a minute.
All you need to do is add your company’s main domain name to the platform as a seed asset.
Our platform then starts the process of discovering your organization’s external attack surface, mapping it, exploiting it, and generating alerts based on criticality for smart prioritization and remediation.
Element Security vs other CTEM platforms
| Feature | Element Security | Other CTEM platforms |
| Installation time | Instant | Variable |
| Agent required | No | Yes |
| Scoping coverage | Unlimited | Limited |
| Scanning frequency | Daily | Weekly to monthly |
| CTEM coverage | Complete | Partial |
| Active exploitation | Yes | No |
| Validation | Active | Passive |
Functionally, no installed agent is required. Element Security CTEM platform can work from a corporate email address/domain name and is managed through a SaaS-style dashboard.
Element Security can also be integrated with existing ticketing and reporting systems to coordinate alerts.
See Element Security’s CTEM Platform In Action
Take control of your external attack surface with the only full-cycle CTEM platform on the market.
Try a free demo of Element Security.