Based on our experience in external attack surface management (EASM) and continuous threat exposure management (CTEM) solutions, understanding the gap between the CTEM framework and EASM requires considering what happens after asset discovery.
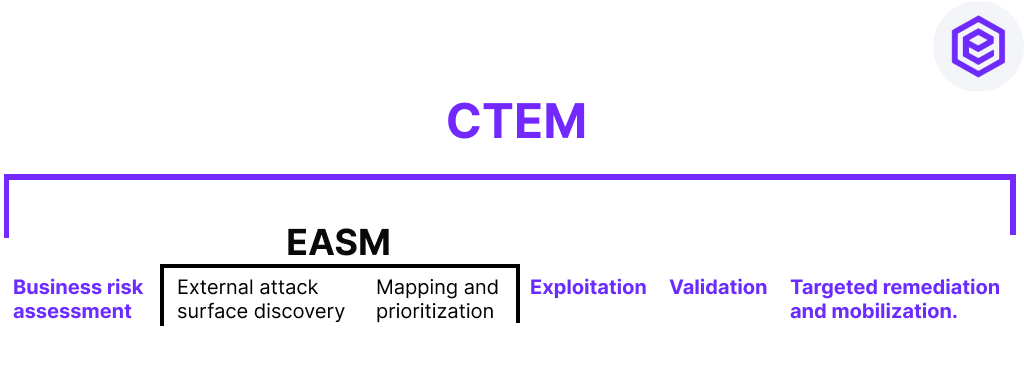
The CTEM framework is based on asset discovery and validating threat exposure through attack vector exploitation to adapt remediation prioritization to the business impact of a breach. EASM, on the other hand, focuses on asset discovery, often relying on the common vulnerability scoring system (CVSS), or, in the best case, on the exploit prediction scoring system (EPSS) to evaluate vulnerabilities’ severity. This reliance on generic scoring standards is devoid of contextual exposure evaluation. The result is a flood of false positives and an underestimation of low scored vulnerabilities with a high impact on business critical assets.
In other words, EASM only covers the discovery stage of the CTEM framework and more comprehensive tools are needed to meet the CTEM standard.
External attack surface management
External attack surface management (EASM) continuously identifies, monitors, and manages an organization’s external-facing digital assets. discovers vulnerabilities in external attack surfaces.
Continuous threat exposure management
The CTEM framework is not limited to discovery. Its five stages cycle consists of scoping – an executive decision of the scope on which to apply the CTEM approach -, discovery – detecting and mapping all assets, validation – launching attacks to evaluate the exposure severity-, prioritization – optimizing mitigation schedule based on contextual exposure -, and remediation.
| Type | CTEM | EASM |
| Definition | Continuous discovery, scoping, prioritization, mobilization, and validation of attack surface exposure | Continuous asset discovery and mapping |
| Validation | Yes | No |
| Prioritization | Contextual | Generic |
| False Positives | Low | High |
| Comprehensive | Multi-stage cyclic framework covering scoring vulnerabilities based on their
contextual exposure and breach business impact. |
Limited to external asset discovery and mapping |
External attack surface management (EASM) vs continuous threat exposure management (CTEM)
The rest of this article further breaks down the differences between CTEM and EASM.
EASM takes a theoretical approach to risk discovery and prioritization
Business requirement and technological progress have expanded and complexified external attack surfaces. Digital facing attacks now include cloud and SaaS stored data, SaaS, known, unknown, unmonitored, and leaked credentials, etc. that risk exposing valuable data or being used as an initial access entry point.
The expansion of new technologies reflecting evolving needs results in a constantly shifting attack surface. In parallel, monitoring all assets, such as web applications, APIs, cloud services, and internet-connected devices, across multiple locations and managed by different teams, is a logistical nightmare.
EASM platforms address some elements of that problem by automatically identifying – and sometimes mapping – digital-facing assets and their vulnerability. However, the vulnerability scoring process is likely to generate multiple irrelevant alerts and miss out on genuinely critical exposure with a low generic severity score. Without a contextual readjustment, generic vulnerability scoring generates numerous false positives, which increases alert fatigue, and ignores high-risk entry points with a misleading low score.
→ Relying on EASM alone generates numerous false positives, resulting in a misleading perception of the external attack surface security posture.
The problem with how EASM presents data to security teams is twofold.
- A theoretical vulnerability scoring approach generates an onslaught of alerts unrelated to their actual severity.
- Under-evaluated critical vulnerabilities are not prioritized accurately, slowing down their actual mitigation and leaving them open to breach.
One of the CTEM framework aims is to rectify the misguiding vulnerability scores of cthe lassic external attack surface exposure management process.
CTEM validates exposures’ severity with adversarial assessments and redefines remediation prioritization based on contextual exposure.
While EASM and CTEM are both continuous processes, the recommended CTEM cycle is far more comprehensive.
EASM takes a broad approach to asset discovery while CTEM correlates the impact of a breach with exposed assets’ business value and pinpoint business-critical exposure.
From there, CTEM scans outward to discover the public-facing assets connected to these parts of the environment. The scanning happens in the same way as EASM and is also automated.
However, once the CTEM discovery phase returns a prioritized list of risks, those exposures are validated to see if they are exploitable. Potential risks like misconfigured cloud instances or vulnerable web forms are tested with the same attack vectors mimicking threat actors’ techniques.
The results from this testing are used to sort risks based on their true severity and map out exploitation paths that need to be fixed. This process is called validation and is an essential part of the CTEM process that does not feature in EASM.
→ Validation is the process of assessing vulnerability exploitability in context through launching attacks.
Validating risks is a key advantage of the CTEM process over EASM because vulnerabilities or misconfigurations in external assets will create very different levels of risk based on their environmental setting.
An asset with a vulnerability scored by CVSS as critical might be irrelevant in context. Even a high exploit prediction scoring system EPSS) might be over or under-evaluated. Adopting a CTEM framework prevents alert fatigue or ignored underestimated exposure risk. However, a framework is a theoretical concept. As CTEM is neither a technique nor a tool, its practical implementation is challenging.
These vulnerabilities’ severity vary widely from environment to environment. That’s why prioritization based on generic scores is not good enough, and true attack surface risk reduction requires validation.
→ CTEM combines comprehensive mapping of internet-facing assets’ business value with their adversarially validated contextual criticality and provides a vital metric to prioritize remediation schedule.
Mobilization is another EASM vs CTEM difference
The CTEM framework mobilization stage is where resources are allocated to the mitigation process. There is no mobilization stage in EASM, so adopting the CTEM framework will require additional tools, with a risk of worsening tool sprawl.
→ CTEM ensures that resources are allocated according to prioritized tasks.
Deploy Rapid CTEM Benefits In Your Environment
According to Gartner, organizations that follow the CTEM framework will experience 3x less breaches.
The most rapid and effective way to get CTEM benefits is to use solutions, such as the Element Security platform, that implement the CTEM framework.
Element Security platform works with no agent, no deployment, and no implementation. Within minutes of activation, it automatically discovers digital-facing assets and validates your external attack surface exposure. It is a full-cycle CTEM capability in a single solution.
Try a free demo to see how easy it is to get CTEM benefits in your environment.
CTEM vs EASM FAQs
Is an EASM solution required for CTEM?
An EASM solution can be included in the CTEM framework discovery stage. However, it lacks many of the capabilities required to implement CTEM.
Is CTEM better than EASM?
CTEM is a framework and EASM might be integrated in CTEM implementation but only in the discovery stage.
What does EASM lack to align with CTEM
EASM lacks the capabilities required in CTEM validation, prioritization, and mobilization stages.