The biggest difference between CTEM and ASM is validation. With Continuous Threat Exposure Management (CTEM), risks are always validated; with Attack Surface Management (ASM), risks are theoretical.
We explain this difference in more detail further down, but to understand CTEM vs ASM, it helps to think about how the idea of ASM came about in the first place.
The concept took siloed functions like network scanning and vulnerability management and combined them into a consolidated process.
CTEM does the same thing to ASM.
CTEM is a systematic approach to cyber risk reduction that zooms out from what ASM does to include:
- Business-wide assessment of potential sources of cyber risk.
- Prioritization and validation of risks discovered during attack surface discovery and management.
- Stakeholder involvement in risk reduction.
And more.
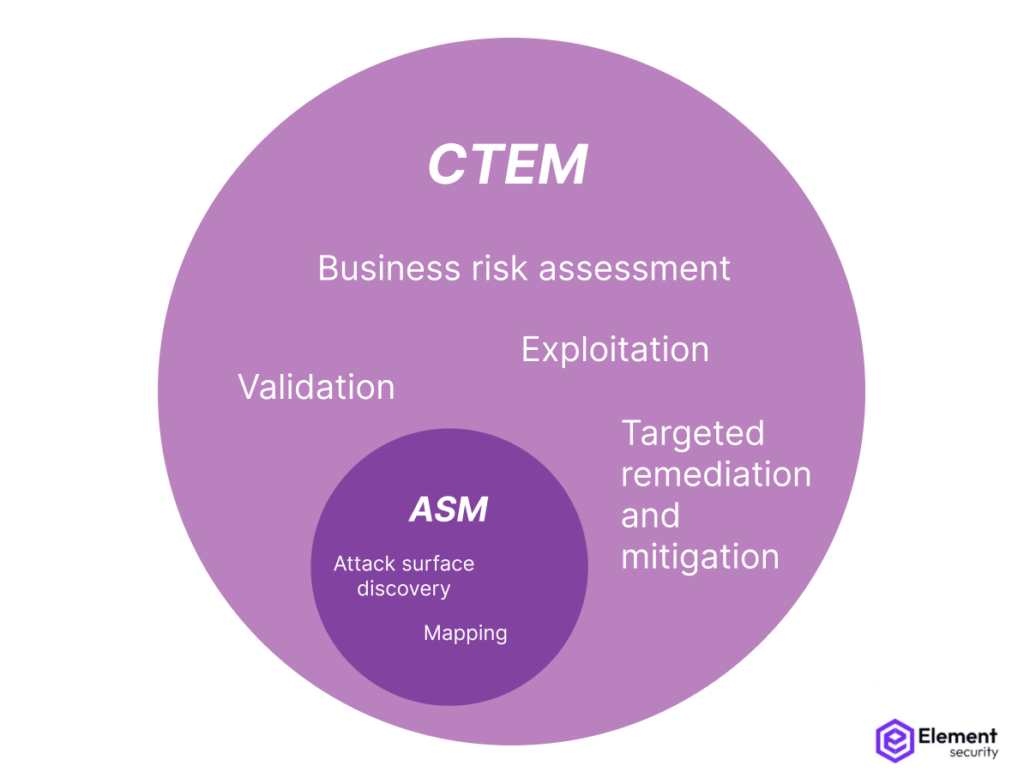
At a high level, CTEM is a superset of ASM.
For security leaders, it’s important to understand this difference but also to know what separates CTEM and ASM on the market today. Some of the solutions that describe themselves as CTEM or ASM (or BAS or XYZ, the list goes on) can appear to have significant overlaps in capabilities.
As a result, the market can be a confusing place for buyers trying to figure out whether an ASM solution or a CTEM platform is a better fit for their risk reduction goals.
Our advice for anyone considering CTEM vs ASM – whether in terms of a solution type or process – is to choose CTEM. Forget about acronyms and focus on capabilities. CTEM does more than ASM and, as a result, allows security teams to do less while getting more secure in the process.
The rest of this blog post explains why and goes into more detail about ASM vs CTEM from a security solutions viewpoint.
What Is CTEM?
At a high level, Continuous Threat Exposure Management (CTEM) is the discovery, scoping, prioritization, mobilization, and validation of attack surface risks done continuously. It is a process.
Gartner, who defined CTEM in 2022, says that by 2026, organizations that focus their security investments on an ongoing exposure management program will be three times less likely to experience a breach.
The concept of CTEM has evolved to become one of the most promising cybersecurity developments of the last several years.
CTEM is a continuous risk reduction process with five interlinked stages
CTEM solutions include CTEM platforms like Element Security that allow security teams to consolidate and automate CTEM processes. CTEM results in a map of validated, proven cyber risks and a plan to mitigate or remediate them.
ASM vs CTEM Solutions
ASM involves the discovery and prioritization of assets but does not involve the validation of risks as CTEM does.
The core difference is that with CTEM, security teams get proof that ASM findings are valid, i.e., that the risks flagged during attack surface discovery and mapping will actually exist when they investigate further.
| Solution Type | CTEM | ASM |
| Definition | The discovery, scoping, prioritization, mobilization, and validation of attack surface risks done continuously. | The discovery and prioritization of assets without validation. |
| Process Involved | Discovery, scoping, prioritization, mobilization, and validation of attack surface risks. | Discovery and prioritization of assets without the validation step. |
| Validation of Risk | Yes. Validates theoretical findings by actually testing and exploiting vulnerabilities. | No. Does not involve validation; findings remain theoretical and untested. |
| Results | Realistic. Provides proof of real risks by exploiting vulnerabilities. | Theoretical. Findings are theoretical, logged as potentially exploitable without proof. |
| False Positives | Low. Reduced due to validation; more precise and generates less noise. | High. Higher possibility of false positives; may report issues not actually dangerous.¸ |
ASM typically involves discovering assets connected to a corporate network and logging potential vulnerabilities that are theoretically exploitable and risky. However, no actual proof of that risk is created during the ASM process.
The outcome of an ASM process is a list of theoretical risks present in an organization’s attack surface.
ASM findings are theoretically correct but may not be actually dangerous or exploitable. Due to filter issues, an ASM solution can produce alerts based on versions or expired certificates, etc.
Why Validation Matters When Comparing CTEM vs ASM Solutions
CTEM is a broader process than ASM, but, as we’ve already explained, the core difference between CTEM and ASM solutions is validation.
To do validation, you need to not only discover potential attack vectors but also test them. In other words, there needs to be attack vector exploitation.
After a very deep mapping stage including both applications and network infrastructure, a CTEM solution, like Element Security, can use an exploit engine to sense which asset is relevant to an organization’s threat landscape and risk profile and pull the right attack vector from its database to test the asset realistically.
As a result, the mapping findings from the initial stage of CTEM are validated.
While ASM solutions can do attack surface mapping, they do not, as a rule, validate their findings. As a result, ASM can create a lot of false positives. This matters because false positives are becoming one of the greatest threats to security teams, causing burnout, wasting resources, and leading to real threats being ignored or missed.
CTEM solutions cut false positives by validating risks and are a highly efficient way to test your network environment and guide mitigation and remediation efforts.
CTEM Is All About Prioritization
Because CTEM validates issues, your security team can properly prioritize their work based on a real-time understanding of criticality, not just speculation.
CTEM helps security teams pinpoint where to spend their time and resources.
Try a free demo of Element Security today.