DORA compliance software can automate many Digital Operational Resilience Act (DORA) information and communication technology (ICT) requirements.
We’ve done extensive research into DORA documentation and the latest DORA updates.
Based on what we’ve seen, a CTEM platform is a great choice for DORA compliance software.
CTEM DORA compliance software can help automate DORA risk identification, management, and testing requirements – turning complex manual compliance tasks into an automated, continuous workflow.
This blog post explains how CTEM compliance software like Element Security fits into DORA compliance programs.
DORA Compliance Depends On Continuous Assessment of Risk
DORA’s ICT requirements primarily focus on cyber risk identification, mitigation, and testing.
The keyword here is “risk.”
Companies ranging from Spanish fintech startups to German multinational banks need to be able to find, track, and communicate their evolving cyber risks.
In DORA chapter 2 (ICT risk management) and chapter 4 (Digital operational resilience testing), this goal is further broken down into a long list of high-level cybersecurity requirements.
Organizations within DORA’s scope will have to meet specific requirements, like being able to:
- “Address ICT risk quickly, efficiently and comprehensively.”
- Provide complete and updated information on ICT risk and on their ICT risk management framework to the competent authorities upon their request.”
- Develop an ICT risk management framework that will be “continuously improved on the basis of lessons derived from implementation and monitoring.”
And more. You can read a full list of DORA requirements here.
The common thread between the requirements in Chapter 2 and other DORA ICT-relevant chapters is being able to discover ICT risks, mitigate them, and track how effectively your security controls are working.
The EU, via DORA, wants FSI companies to continuously monitor and test their attack surface.
Meeting these requirements will be very difficult without using DORA compliance software like a CTEM platform.
Taking a risk-based approach means looking at your ICT environment from an attacker’s perspective. Specifically, this involves identifying real-world weaknesses and being able to answer questions like, “Where are potential exploitation paths being created in our environment, and how are we fixing them?”
Where Organizations Without DORA Compliance Software Will Struggle
Taking a risk-based approach to cybersecurity (as per DORA) traditionally meant a workflow that looked something like this:
1. Regular vulnerability scanning to find vulnerabilities.
2. Manual prioritization of the CVEs found.
3. Deploying controls to cover or installing patches to fix those CVEs.
4. Pen testing to prove mitigation works.
5. Red teaming to get an overall viewpoint of cyber security performance.
The process above is, for the vast majority of organizations, neither affordable nor scalable.
Only a small minority of organizations are doing consistent pen testing of their external networks. Fewer still are doing pen testing monthly or more frequently (essential for keeping up with risks). The result is that 96% of companies are vulnerable to external attacks.
While DORA will require some organizations to do threat-led penetration testing, a kind of red teaming exercise, all covered organizations will need to test their cybersecurity controls to some level.
For most, the best solution to DORA compliance is automation.
A technological solution like a continuous threat exposure management (CTEM) platform can help your DORA compliance program by:
1. Discovering attack surface risks, including CVEs.
2. Testing those risks based on threat intelligence and using realistic exploitation paths and payloads.
3. Prioritizing testing results so remediation teams can plan work.
4. Continuously retesting and showing the results of remediation and the progress made.
With the above workflow, an organization can ensure DORA compliance regardless of how the law evolves. Like the General Data Protection Regulation (GDPR), we predict that DORA will undergo significant changes in the next few years.
However, the core goal of being able to continuously assess risk and track mitigation progress will remain. Companies that get this right will not struggle with compliance.
Solving DORA Requirements with a CTEM Platform
CTEM is the process of continuous threat exposure management.
It is a proven method for organizations to rapidly and sustainably understand their attack surface and comply with the ICT requirements of DORA, including identifying assets, validating security controls, testing ICT tools, communicating risk management, testing systems, and more.
A CTEM platform allows organizations to automate the risk discovery, testing, and prioritization that DORA requires.
With CTEM, an organization can discover network-connected assets, test them for risk, prioritize them for remediation, and map remediation workflows as a single process.
The benefits are rapid, too. The market’s leading CTEM platform, Element Security, can be deployed in minutes.
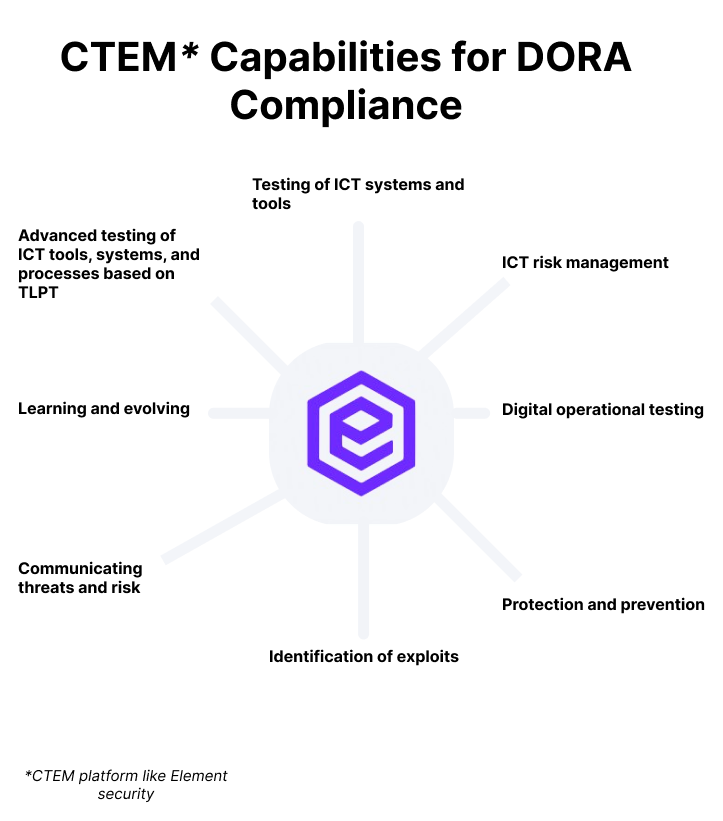
Matching CTEM Capabilities to DORA ICT Requirements
This section maps Element Security’s CTEM platform’s capabilities to some core DORA requirements.
Note: This is an executive summary. A full analysis of Element Security’s ability to bridge DORA compliance gaps would cover most of the ICT requirements in Chapters 2 and 4. Contact us for a free demo to see how this would work in your environment.
| DORA Requirement | CTEM capability |
| Chapter 2, Article 6: ICT risk management framework | See real-world evidence about how effective your security controls are. Element Security discovers IT assets and tests them with real payloads in a continuous, risk-free way. The results can be used to create and update the risk management framework required by DORA and to communicate progress with regulators. |
| Chapter 2, Article 7: ICT systems, protocols, and tools | Validate the security of ICT systems, protocols, and tools by combining asset discovery and vulnerability with realistic exploitation in a single pane of glass. |
| Chapter 2 Article 8: Identification | Discover known and unknown network-connected ICT assets and assess them for exploitable vulnerabilities with Element Security’s CTEM Platform. Realistic exploitation allows security teams to find exploitation pathways and discover the root causes of risks. |
| Chapter 2 Article 9: Protection and prevention | Real-world testing that automatically and continuously validates how well security tools, policies, and procedures work. |
| Chapter 2, Article 13: Learning and evolving | A single solution for gathering information on vulnerabilities and cyber threats to external facing network assets and analyzing the impact they are likely to have on digital operational resilience. |
| Chapter 2, Article 14: Communication | Automated reporting on threat intelligence and vulnerability detection. A single platform for immediately assessing the risk of new vulnerabilities like Log4j. |
| Chapter 4, Article 24: General requirement for the performance of digital operational resilience testing | Automate external network penetration tests and track mitigation and how successful risk reduction (“corrective measures” as per DORA) are. |
| Chapter 4, Article 25: Testing of ICT tools and systems | Perform automated test execution, including vulnerability assessments and scans, network security assessments, gap analyses, scenario-based tests, performance testing, and penetration testing of ICT tools and systems. Identify vulnerabilities and assess network security with the Element Security CTEM platform. |
| Chapter 4 Articles 26: Advanced testing of ICT tools, systems, and processes based on TLPT | Automate and scale red team reconnaissance as part of the TLPT testing phase. Emulate real adversary techniques and full attack paths on live production systems. Element Security is a powerful software solution for preparing for threat-led penetration testing (TLPT). |
See Element Security’s CTEM Platform In Action
Supercharge your DORA compliance program with a fit-for-purpose CTEM software solution.