Part 1: From VM to Exposure Management
Exposure management (EM) is the new vulnerability management (VM). VMs gradually became unwieldy due to the exploding number of vulnerabilities that led to an unmanageable patching backlog epidemic. To solve that problem, entrepreneurial startups started creating exposure management platforms under various names. In 2022, Gartner crystallized the exposure management terminology with its continuous threat exposure management (CTEM).
This blog aims to make sense of the different aspects of CTEM and how the two latest emerging technologies, Adversarial Exposure Validation (AEV) and Exposure Assessment Platforms (EAP), fit in.
Why the move from VM to EM
The switch from VM to EM moves the mitigation focus from the vulnerabilities’ potential severity to their actual exploitability. VM relies heavily on the Common Vulnerability Scoring System (CVSS) to prioritize vulnerability management. It is based on a formula with several metrics that approximate the ease and impact of an exploit targeting the common vulnerabilities and exposures (CVEs). The proliferation of CVEs challenges the effectiveness of relying exclusively on CVSS scores to identify exposure.
The exponential growth of CVEs
The CVSS-based approach focuses on the theoretical risk posed by CVEs but ignores the existence or, more importantly, the non-existence of a corresponding exploit. Over 40,000 CVEs were published in 2024 alone, 38.83% more than in 2023 and 15,32 % of all CVEs since the CVE standard creation in 2009. Even focusing exclusively on CVEs with a score of 8 and above would translate into 10,543 CVEs in 2024, or 28 per day. 2025 promises to be even worse.
So focusing on exploitable CVEs is not an option anymore, it is an absolute necessity.

Case in point, CISA reports that “many vulnerabilities classified as ‘critical’ are highly complex and have never been seen exploited in the wild less than 4% of the total number of CVEs have been publicly exploited. But those need an immediate patching. threat actors are extremely quick to exploit their vulnerabilities of choice. CISA warns that “of the 4% known exploited CVEs, 42% are being used on day 0 of disclosure; 50% within 2 days; and 75% within 28 days.”
From CVEs to KEVs
To address this issue, in November 2021, CISA created the Known Exploited Vulnerabilities (KEV) catalog. KEVs adjust CVSS scores based on known exploited vulnerabilities to point at CVE that must be patched first. In comparison with the average of 3270 CVEs added monthly in 2025, there was a total of 185 new KEVs in 2024 and 187 in 2023. Interestingly, the 2024 KEV catalog includes CVEs dating back to as far as 2012.
Though KEV is a welcome improvement on CVSS, it still suffers from major shortcomings. Every new KEV needs to go through the cumbersome and time-consuming CIS requirements. CISA requires proof of active exploitation, availability of remediation guidance, assignment of CVE identifier, and severity of the vulnerability exploitation. Failing to answer any of those excludes KEVs from the list.
Yet, even with a patching load prioritized with KEVs, the median total time for remediation (MTTR) is 174 days. This is much faster than non-KEV MTTR (621 days), but it is still far too slow to stay ahead of attackers’ exploitation speed, as reported by CISA, which peaks at 28 days.
The exponential growth of asset sprawl and the uniqueness of any organization’s system architecture are challenging the recent KEV scores’ relevance in an organization system’s context.
The tentacular data sprawl
Global trends show a spectacular and steady growth in data production.
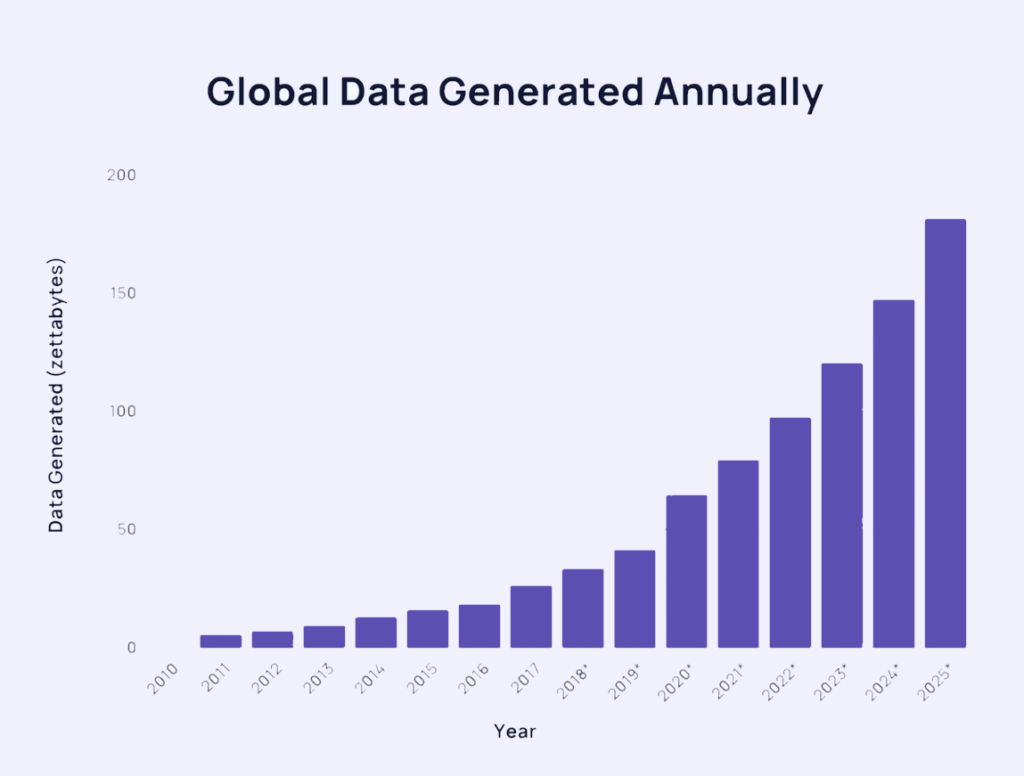
Inside organizations, 90% of business-critical documents are shared outside the C-suite, and over 15% of all business-critical files are at risk from oversharing, erroneous access permissions, and inappropriate classification.
The majority of this data is unstructured and includes 251 different types of business-critical categories. To compound the problem, the business advantages of using multiple providers for cloud services spread data across many supports.
Environment-specific risk factors
The uniqueness of systems architecture is the other factor that curtails KEVs’ score effectiveness. The same vulnerability can have different severity levels depending on the system architecture. A vulnerability that is theoretically exploitable is not necessarily actually exploitable. Compensating controls that prevent known exploits from using that vulnerability renders it unexploitable.
Ad hoc, unique configurations might be best suited to answer business priorities, but they lead to non-standard deployments (e.g., custom APIs, hybrid cloud environments) that increase the likelihood of undetected critical exposures.
This dynamic and ever-expanding attack surface is ill-suited for traditional generic score-based patching prioritization and demands in context severity evaluation.
KEVs include the parts of the exploitability factor but fall short of the contextual factor. It is undoubtedly a big step in the right direction. However, not only is the inclusion in the KEV catalog dependent on the existence of clear remediation guidance and assigned CVE ID in addition to active exploitation, it might take months to be added.
VM vs EM
The term exposure covers any security gap that a cyber-attacker could use as an entry point into a digital infrastructure or leverage for escalation after establishing an initial foothold. In addition to vulnerabilities, they include misconfigurations, open ports, outdated certificates, unpatched systems, improperly documented versioning, stolen credentials, improperly configured compensating controls, and more.

Managing exposures far exceeds the limits of managing vulnerabilities and cannot be contained by the vulnerability management concept. Threat exposure management implies adopting an adversarial stance to look at an attack surface from an attacker’s point of view.
According to Gartner, “Through 2028, adversarial exposure validation capabilities that simulate live attack scenarios will become accepted alternatives to traditional penetration testing exercises required by regulatory frameworks.”
Part two – From TEM to Adversarial Exposure Validation (AEV) and Exposure Assessment Platforms (EAPs) delves deeper into the intricacies of exposures and how they are tackled.